Show more
Sort by
Newest
Oldest
Popular
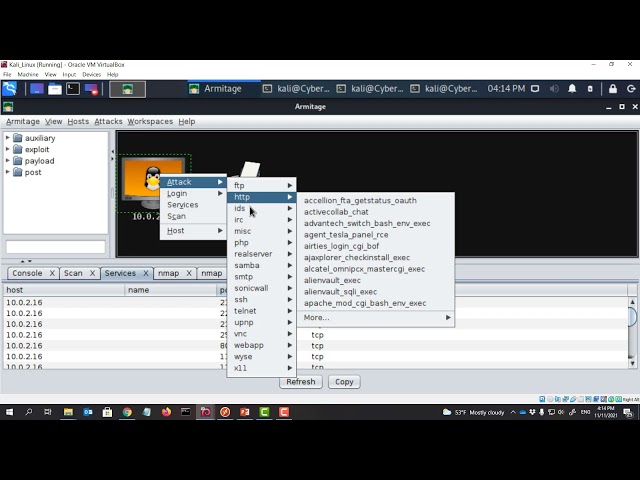
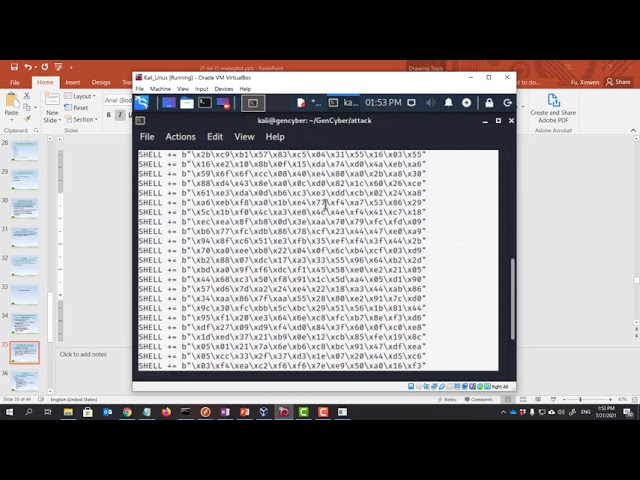
Create a new metasploit module
777 views
Enable https with Apache at Ubuntu
1,116 views
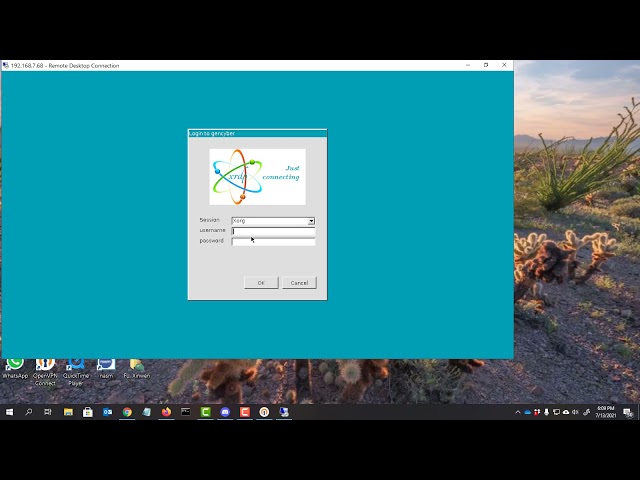
SurfacePro RDP into Kali VM
55 views
John the ripper
56 views
Backdooring Putty
152 views
Vulnserver chat via Telnet
48 views