Sort by
Newest
Oldest
Popular
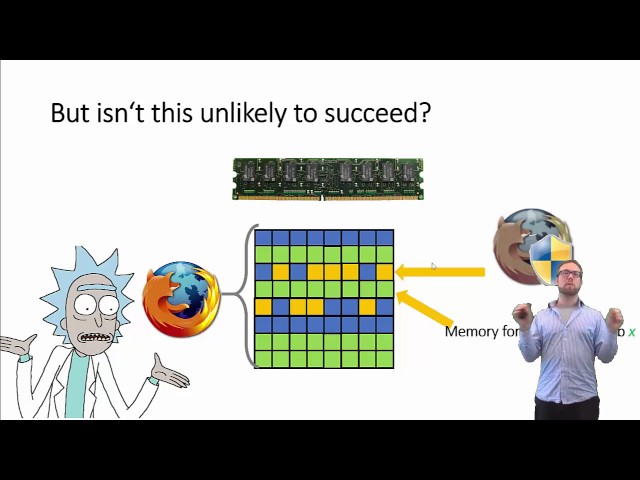
Rowhammer attacks explained simply
28,715 views

CS453 - Secure design
387 views
CS453 - Heap overflows
2,277 views

CS453 - How to write a shellcode
3,943 views
CS453 - Buffer overflows
1,460 views
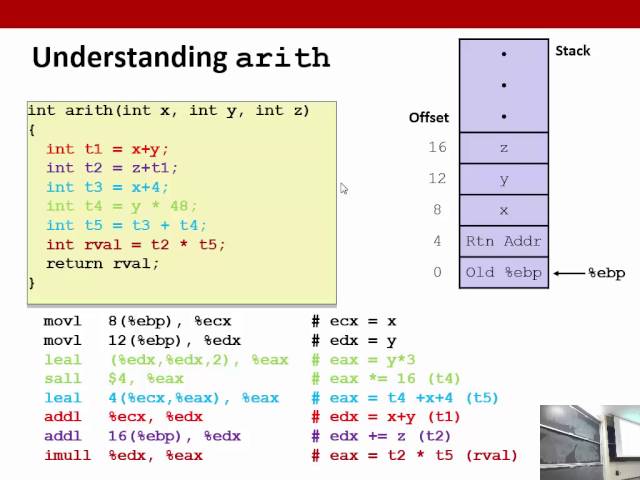
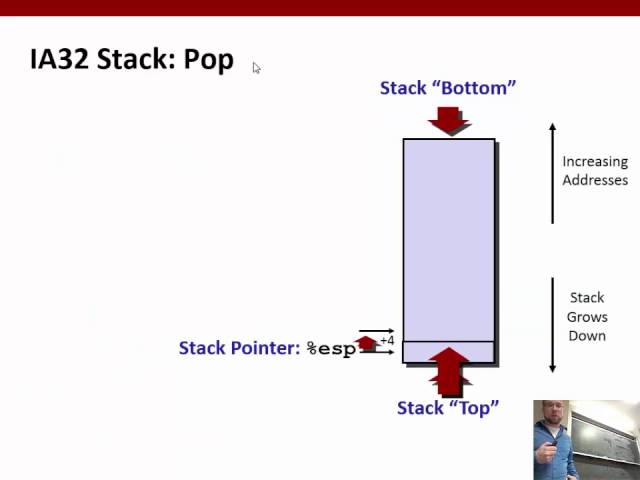
CS453 - x86 assembly, part 2/3
1,517 views

CS453 - x86 assembly, part 1/3
4,133 views

CS453 - Network Security
532 views

CS453 - RSA and Randomness
548 views