Applied Cryptology Lectures, Fall 2022 Semester

Historical Ciphers
0 views

Frequency Analysis
0 views

Playfair Cipher
0 views

Unbreakable Cipher
0 views

Real World Cryptanalysis
0 views

Block Cipher Design
0 views

PRESENT Block Cipher
0 views

Password Cracking
0 views

CAESAR Competition
0 views

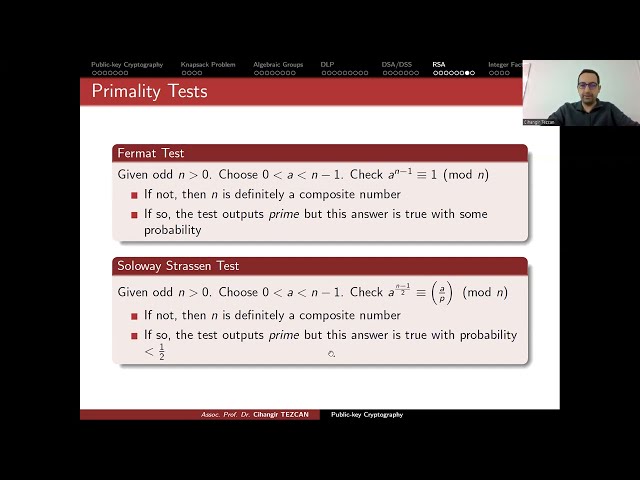
Public-key Cryptography
0 views

Public Key Certificate
0 views